Over the past few days
Emsisoft’s malware research team has received numerous reports of a new
file encrypting ransomware strain. This new family of ransomware is
commonly referred to as CryptoLocker or Trojan:Win32/Crilock.A.
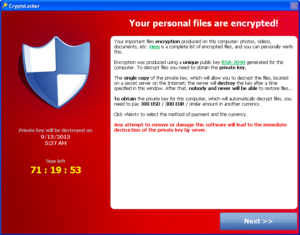
Like all file encrypting ransomware (also known as crypto malware) the goal of the attacker is to encrypt important files on the victim’s system in order to compel them to pay a ransom in return for their files.
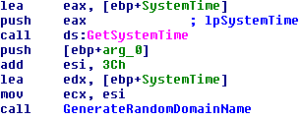
If that fails the malware will start generating seemingly random domain names using a domain generation algorithm. This is done by creating a seemingly random string of characters based on the current system time and prepending it to one of the following seven possible top level domains:
HTTP merely acts as a wrapper though. All actual data exchanged during the communication between the bot and its command and control server is encrypted using RSA. The public key used for the encryption of the communication is thereby embedded inside the malware file. Using RSA based encryption for the communication not only allows the attacker to obfuscate the actual conversation between the malware and its server, but also makes sure the malware is talking to the attacker’s server and not a blackhole controlled by malware researchers.
The command and control server replies with the victim’s IP address, as well as a unique RSA public key, that will be used by the malware during the further encryption process.
As soon as the infection specific RSA key has been obtained, the malware will look for files to encrypt. It does so by searching through all connected drives, including mapped network shares, for files matching one of the following patterns:
Based on the file types list, it is also clear that business users are specifically targeted. Crypto malware intended for home users will target music, picture, and video files. This malware though primarily targets file formats used by companies, completely ignoring common home user file types.
In order to clean the actual infection, run a full scan with Emsisoft Anti-Malware or the Emsisoft Emergency Kit and quarantine all detected objects.
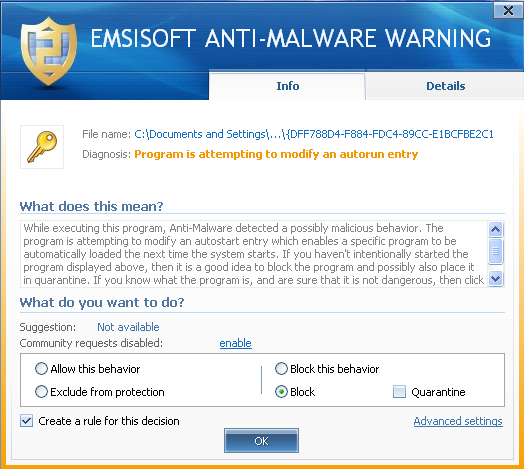
Users of Emsisoft Anti-Malware or Online Armor are not at risk of falling victim to either CryptoLocker or the malware downloader from the initial email campaign, unnoticed, as both are no match for our award winning behavior blocking technology.
http://blog.emsisoft.com/2013/09/10/cryptolocker-a-new-ransomware-variant/
Like all file encrypting ransomware (also known as crypto malware) the goal of the attacker is to encrypt important files on the victim’s system in order to compel them to pay a ransom in return for their files.
Initial infection and establishing communication
Based on the data we have gathered so far, the infection is mainly spread via social engineering techniques. Multiple victims received emails with alleged customer complaints containing an attachment that is in fact a malware downloader. This downloader then downloads and installs the actual CryptoLocker malware. Once CryptoLocker has been downloaded and executed by the downloader, it ensures its automatic start during boot by using the following registry value:- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
CryptoLocker = %appdata%\{CLSID}.exe (note that the file name consists of random hexadecimal numbers).
If that fails the malware will start generating seemingly random domain names using a domain generation algorithm. This is done by creating a seemingly random string of characters based on the current system time and prepending it to one of the following seven possible top level domains:
- .com
- .net
- .biz
- .ru
- .org
- .co.uk
- .info
- xeogrhxquuubt.com
- qaaepodedahnslq.org
HTTP merely acts as a wrapper though. All actual data exchanged during the communication between the bot and its command and control server is encrypted using RSA. The public key used for the encryption of the communication is thereby embedded inside the malware file. Using RSA based encryption for the communication not only allows the attacker to obfuscate the actual conversation between the malware and its server, but also makes sure the malware is talking to the attacker’s server and not a blackhole controlled by malware researchers.
File encryption
Once the system has been successfully infected and a communication channel to the command and control server has been established, the malware will start the encryption process by requesting an encryption key. A typical request includes the version of the malware, a numeric id, the system’s network name, a group id as well as the language of the system.The command and control server replies with the victim’s IP address, as well as a unique RSA public key, that will be used by the malware during the further encryption process.
As soon as the infection specific RSA key has been obtained, the malware will look for files to encrypt. It does so by searching through all connected drives, including mapped network shares, for files matching one of the following patterns:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd, *.cdr, ????????.jpg, ????????.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7cFor each file matching one of these patterns, the malware will generate a new 256 bit AES key. This key will then be used to encrypt the content of the file using the AES algorithm. The AES key is then encrypted using the unique RSA public key obtained earlier. Both the RSA encrypted AES key, as well as the AES encrypted file content together with some additional header information are then written back to the file. Last but not least the malware will log the encryption of the file within the HKEY_CURRENT_USER\Software\CryptoLocker\Files registry key. This key is later used by the malware to present the list of encrypted files to the user and to speed up decryption.
Based on the file types list, it is also clear that business users are specifically targeted. Crypto malware intended for home users will target music, picture, and video files. This malware though primarily targets file formats used by companies, completely ignoring common home user file types.
Decryption
Unfortunately, once the encryption of the data is complete, decryption is not feasible. To obtain the file specific AES key to decrypt a file, you need the private RSA key corresponding to the RSA public key generated for the victim’s system by the command and control server. However, this key never leaves the command and control server, putting it out of reach of everyone except the attacker. The recommended solution is to restore encrypted files from a backup.In order to clean the actual infection, run a full scan with Emsisoft Anti-Malware or the Emsisoft Emergency Kit and quarantine all detected objects.
Prevention
Especially when decryption of encrypted files is impossible, prevention is of the utmost importance. An offline backup as well as adequate protection are imperative.Users of Emsisoft Anti-Malware or Online Armor are not at risk of falling victim to either CryptoLocker or the malware downloader from the initial email campaign, unnoticed, as both are no match for our award winning behavior blocking technology.
http://blog.emsisoft.com/2013/09/10/cryptolocker-a-new-ransomware-variant/

No comments:
Post a Comment