A team of researchers created in the lab the Chameleon WiFi virus, a malware that infects entire WiFi networks replicating contagion of a common cold within humans.
A group of security researchers at the University of Liverpool in Britain have provided aproof of concept to demonstrate how to infect an entire WiFi network one shot.
The team of researchers has demonstrated that a WiFi virus, dubbed Chameleon, could be spread within a network like the ‘common cold‘ spreads between individuals, the experts made it possible replacing the firmware of the vulnerable Access Point (AP) with an infected version. Chameleon once infected the Access Point propagate itself to the computers connected to the WiFi network, that can self-propagate overWiFi networks from access point to access point.
The Chameleon malware is a serious threat to IT security, the attack scenario exploits WiFi network and most disconcerting thing is that the attack is undetectable to any defensive mechanism, including Antivirus and Wireless Intrusion Detection System (IDS).
“Hence, this attack is considered advanced and difficult to detect, as IDS rogue AP detection methods typically rely on a change in credentials, location or traffic levels.”
The computer virus is able to identify a weak Access Point and propagates itself with the following steps:
- Establish a list of susceptible APs within the current location
- Bypass any encryption security on the AP.
- Bypass the administrative interface on the AP.
- Identify and store AP system settings.
- Replace the AP firmware on vulnerable APs with the virus-loaded firmware.
- Reload the victim AP system settings.
- Propagate virus (return to 1).
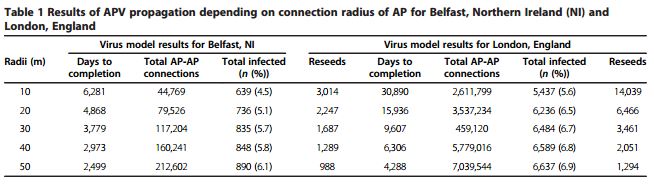
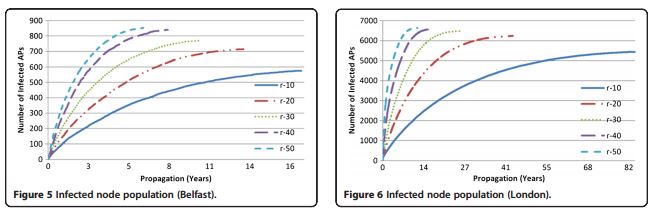
The simulated experiment was conducted to analyze the impact on two cities, Belfast, NI and London, England, their choice is not casual because the example locations chosen represent high- (London) and medium (Belfast)-sized urban environments, based onthe density of APs.
Following the data related to the two regions in which the researchers imagined to have spread the malware.
“The region of Belfast under analysis contains approximately 14,553 APs, of which 22% are open, 61% are WiFi protected access (WPA) 2-encrypted and 14% are WEP-encrypted. The section of London under analysis contains approximately 96,433 APs, of which 24% are open, 48% are WPA/WPA 2-encrypted and 19% are WEP”
The infection starts randomly from one of the access points, the Chameleon virus was able to propagate its self to the overall network within weak APs.
Exactly as in the case of the propagation of the virus among humans, the higher the density of those potential victims, more rapid and extensive is the infection.
“This work demonstrates that AP connectivity density is a more important factor for virus propagation than
product susceptibility “
Those geographical areas with higher density of Access points are more exposed to the contagion.
“WiFi connections are increasingly a target for computer hackers because of well-documented security vulnerabilities, which make it difficult to detect and defend against a virus,” says Marshall, one of the authors of the paper.
The Chameleon virus accelerates in a totally virgin environment, but decelerates as nodes are infected, showing that the risk of an epidemic occurs much earlier than as would otherwise be indicated by the days to completion results.
The paper presents also a method of detecting the Chameleon virus using WiFi layer 2 packet average intervals for beacon frames, it’s clear that technique is specific for the created agent but anyway similar approach could be adopted for malware detection.
Despite Chameleon malware is just an experimental product of the research, there is the concrete risk that in the future the cybercrime will adopt similar strategies to spread malicious code.

No comments:
Post a Comment