Mark Sparshott, director at Proofpoint, explained that cybercrime manages phishing emails using techniques similar to those used by the marketing industry.
Phishing is still considerable on of principal cyber threats for Internet users, it is even more used to spread malware and link to compromised websites, for this reason cybercriminals are adopting new and innovative techniques to make this distribution channel more efficient.
Cyber criminals evaluate with great attention phishing emails, trying to evaluate their level of penetration on target side, as explained by Mark Sparshott, executive director at email security firm Proofpoint, they ‘manage’ phishing emails using techniques similar to those used by the marketing industry. Sparshott referred that cyber criminals behind phishing campaigns perform ‘test audiences’ on the phishing emails to evaluate their effectiveness.
An effective strategy must be able to convince victims to open emails and click on the links they include, the attackers try to profile the audience sending out small bursts of traffic to samples of their desired audience using different templates with different content. They then evaluate the success rate for the different templates, choosing the most successful version for the main email burst.
“Cyber criminals manage the content of their emails to entice clicks,” ”It’s the same technique you might find a leading marketing agency using.”said Sparshott.
Which are the most successful form of email-borne attack?
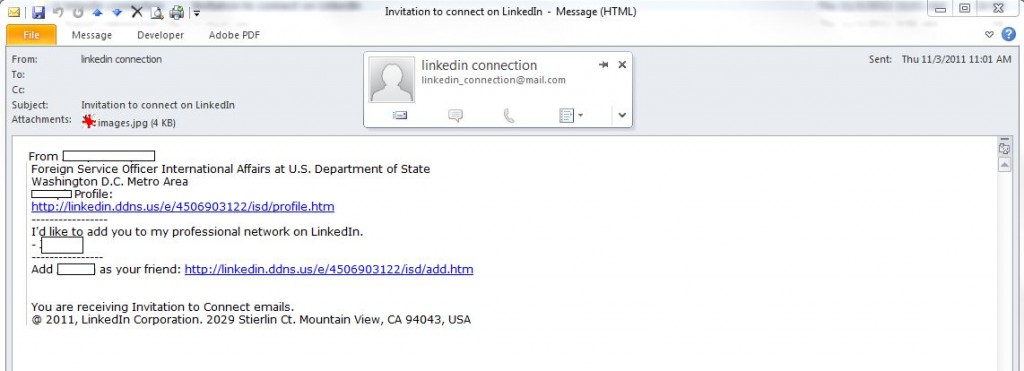
According Sparshott, fake LinkedIn invitations have a click rate double respect phishing email based on banking communications and fake order confirmations.
“The top three which achieve most success are social network communication, financial account warnings and order confirmation. That preys on human curiosity and desire to broaden one’s network, or to not lose money, or to check something you feel you didn’t order.”“The LinkedIn lure is particularly effective, because it can look exactly as if it has come from LinkedIn itself. LinkedIn lures are twice as successful as others, and the most successful is the LinkedIn invitation.”
The goal for cyber criminals is to deceive the highest possible number of victims to click on the link in malicious emails, avoiding human suspicious and of course defense measures including gateway filtering.
“Filtering so much email gives us great visibility of the types of attack out there. We see spear phishing [emails targeting specific individuals, with information about them enticing users to open messages], long lining [a handful of emails targeting a specific organisation, with advanced obfuscation techniques], watering hole [where a website commonly used by the target group is infected with malware] and malvertising [where malware-laden adverts are injected into reputable websites],” is the description of scenario presented by Mark Sparshott speaking at recent Computing‘s IT Leaders’ Forum event in London.“All these attacks leverage clever techniques to bypass traditional reputationand content-based checking at the time of delivery. Once in the inbox, they leverage an understanding of how humans work to make them click the link, where the payloads that attack the system flaws on the device the user is browsing from occur,” he added.
Traditional security systems scan email content searching for malicious content,advanced solutions are also able to scan the links and the sites those links direct users to for anything suspicious. This approach could not be sufficient because at the time the email was delivered, the email, and the sites it links to can all be free of malicious code. In a second phase, once the email passed the checks at “inboxes” side, the cyber criminals add the malware payload to their landing websites.
The analysis proposed by Proofpoint reveals that 10 per cent of users click these links on average, this percentage is alarming and let’s consider that messages succeed toby-pass anti-virus and spam filters.
The rates varied widely between companies, with some firms having a click rate of up to 50%, as a result not all organizations are equally targeted, large entities are hit slightly more than smaller. The experts discovered that membership of an industry is more influential than the size of the victim company.
“The top three which achieve most success are social network communication, financial account warnings and order confirmation. That preys on human curiosity and desire to broaden one’s network, or to not lose money, or to check something you feel you didn’t order.”
As suggested by Sparshott, when you receive invitations in InBox don’t click accept or view it, manage it from the LinkedIn page from a new browser.
No comments:
Post a Comment