Mandiant has released its annual M-Trends 2014 Threat Report, a document that analyzes actors, means and motivations behind attacks observed in 2013.
Mandiant FireEye company has released a new detailed report titled “M-Trends 2014 Threat Report“ describing actors, means and tactics behind principal attacks conducted in the recent months. The report consolidated data on principal cyber threats and also highlights emerging global threat actors targeting different industries.
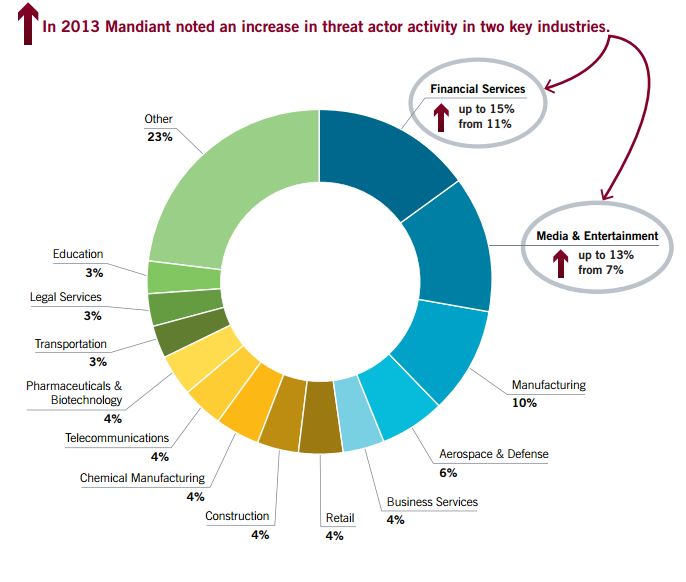
The threats are even more sophisticated, organizations face increasing difficulties to identify the threats and discover a breach on their systems. The industries that most of all have suffered attacks are Financial Services and Media & Entertainment.
How wondering on how companies find that they have been violated, 33% of victims discovered the breach internally (Down from 37% in 2012) while 67% of victims were notified by an external entity. Despite the number of days that threat agents were present on a victim’s network before detection is decreasing (14 days less than 2012), its median number is 229. This data are really scaring in my opinion, bad actors are able to remain undetected within networks of their victims for more than eight months.
“It is hard to overstate how quickly cybersecurity has gone from a niche IT issue to a consumer issue and boardroom priority,” “Over the past year, Mandiant has seen companies make modest improvements in their ability to attack the security gap. On the positive side, organizations are discovering compromises more quickly, but they still have difficulty detecting said breaches on their own. It is our focus to bridge that gap and continue the positive trends our customers are seeing.” said Kevin Mandia, SVP and COO, FireEye.
Phishing is confirmed as one of most insidious cyber threat, attackers prefer to exploit trust in IT departments, curious that the majority of attacks occurs in the same days of the week on Tuesday, Wednesday and Thursday.
“44% of observed phishing emails were IT related, often attempting to impersonate the targeted company’s IT department”
Another interesting aspect in the current threat landscape is the increasing for the effect of political conflicts on private organizations, let consider, for example the effect related to the numerous attacks conducted by members of the Syrian Electronic Army (SEA).
The report dedicates a session on suspected Iran-based threat actors, the hackers appear to be interested to systems and infrastructures of the energy sector and state governments. Mandiant has identified activities that may be attributable toreconnaissance operated by unknown attackers.
The experts at Mandiant hypothesized that that Iranian attackers are state-sponsor hackers conducting surveillance activities, their operations appear less complex than other nation-state actors, but anyway it is important to monitor them.
Iran-based actors used a small set of off-the-shelf tools and a few custom tools which are the result of re compilation of other malicious exploit publicly available. The attackers haven’t used zero-day exploits or custom-written exploits.
“The majority of these suspected Iran-based actors targeted the energy sector. We have also seen these threat actors target the networks of several U.S. state government agencies.” states the M-Trends 2014 Threat Report.
Let’s close the post with a look to Chinese state-sponsored hackers, one year after Mandiant discovered the Chinese cyber espionage group named APT1, it has confirmed that both APT hacking groups, APT1 and APT2, are still active and have resumed their operations.
You just have to read it!


No comments:
Post a Comment